Introduction
In today’s interconnected world, where digital technology penetrates every aspect of our lives, we cannot ignore the importance of cybersecurity.
Cyber threats and attacks are constantly evolving, with potentially devastating consequences for individuals (money theft from bank accounts), businesses (data breach, revenue loss), and even nations (breach of security and availability of life-supporting services).
Here we will explore the significance of cybersecurity, its challenges, and the measures we must take to protect ourselves in this digital age.
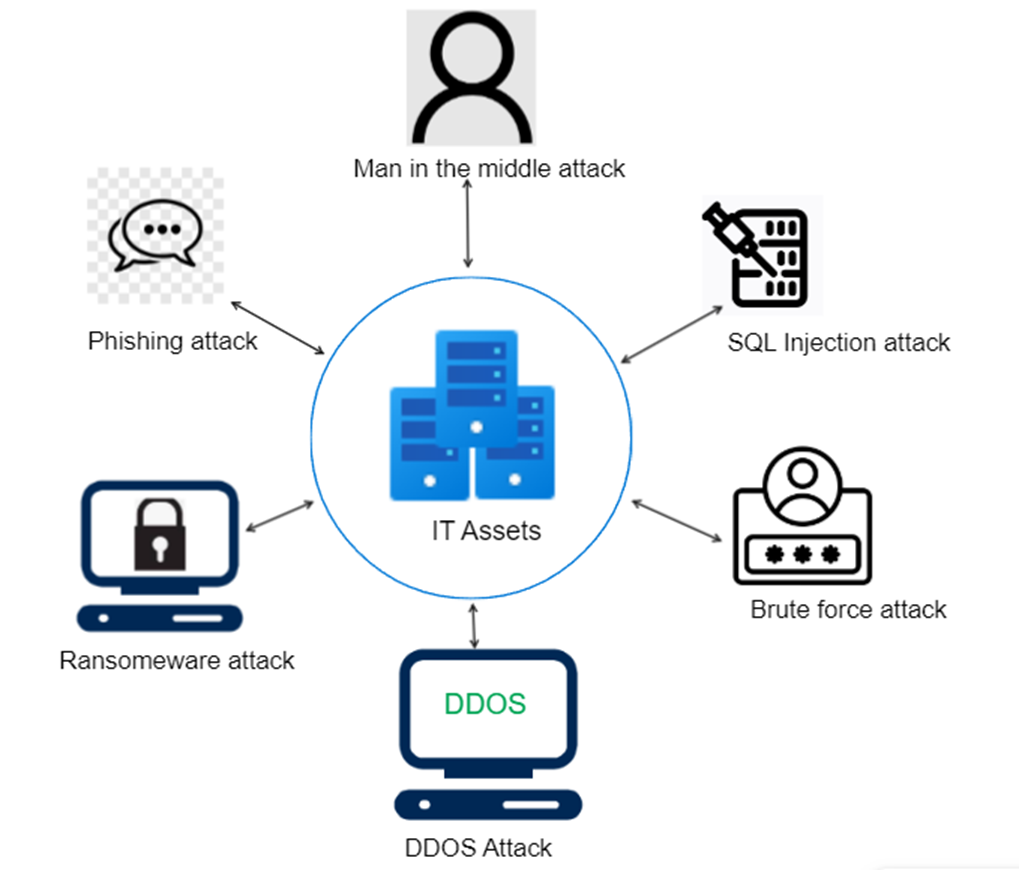
Cybercriminals employ various sophisticated techniques, including phishing, malware, ransomware, and social engineering, to infiltrate systems, steal sensitive data, and create tr
The Implications of Cyber Attacks:
- The consequences of cyber-attacks can be severe and wide-ranging.
- For individuals, the compromise of personal data can lead to identity theft, financial loss, and reputational damage.
- In the business realm, cyber-attacks can disrupt operations, result in financial losses, erode customer trust, and even lead to the downfall of companies.
- Attacks on life-supporting critical infrastructure, such as power grids or healthcare systems, can have profound societal impacts, posing risks to public safety and national security.
Some well-known cyberattacks:
WannaCry Ransomware Attack (2017):
- This was one of the most devastating cyberattacks in history, infecting hundreds of thousands of computers in more than 150 countries.
- The attack exploited a vulnerability in Microsoft Windows operating systems, encrypting users’ files and demanding a ransom payment in Bitcoin to unlock them.
- The total cost of the attack was estimated to be in the billions of dollars, as it affected numerous industries, including healthcare, finance, and transportation.
NotPetya Cyberattack (2017):
- NotPetya was a destructive malware that targeted businesses worldwide, with Ukraine being the primary target.
- The malware spread rapidly, crippling computer systems and causing significant financial losses.
- NotPetya disrupted the operations of numerous multinational corporations, including shipping giant Maersk, pharmaceutical company Merck, and logistics firm FedEx.
- The total cost of the attack was estimated to be over a billion dollars.
Equifax Data Breach (2017):
- Equifax, one of the largest credit reporting agencies in the United States, suffered a massive data breach in 2017.
- The breach exposed sensitive personal information of approximately 147 million people, including social security numbers, birth dates, and addresses.
- This incident led to a significant loss of consumer trust and resulted in numerous lawsuits and regulatory penalties.
- The company’s total losses, including settlements and legal fees, reached billions of dollars.
Sony Pictures Entertainment Hack (2014):
- Sony Pictures Entertainment experienced a highly publicized cyberattack in 2014, allegedly carried out by a group calling themselves the Guardians of Peace.
- The attackers leaked a massive amount of confidential data, including unreleased movies, executive emails, and employee information.
- The attack disrupted Sony’s operations, leading to production delays and reputational damage.
- The estimated cost of the attack, including investigation, remediation, and lost business opportunities, was around $15o million.
Target Data Breach (2013):
- In 2013, retail giant Target suffered a significant data breach during the holiday shopping season.
- Hackers gained access to the company’s network and stole the payment card data of approximately 40 million customers.
- The breach also exposed the personal information of around 70 million individuals.
- Target faced substantial financial losses due to litigation costs, settlements with affected customers, and the implementation of improved security measures.
- The overall impact of the attack on Target’s revenue was estimated to be in the range of several hundred million dollars.
What is cybersecurity?
- Cybersecurity is the collective set of measures and practices designed to protect digital systems, networks, and data from unauthorized access, damage, or disruption.
- It encompasses a proactive approach to identify vulnerabilities, implement protective measures, detect potential threats, and respond swiftly to mitigate their impact.
- Cybersecurity should not be on the back burner, it must be integrated into the fabric of our digital infrastructure.
- Security first should be our approach right from the beginning.
Key elements in cybersecurity strategy
Here, we will talk about some key elements that help us to formulate a comprehensive cybersecurity strategy.

Risk Assessment:
- Organizations and individuals must conduct regular assessments to identify vulnerabilities and potential threats.
- Understanding the specific risks, they face allows for targeted and effective security measures.
Education and Training:
- Cybersecurity is a shared responsibility.
- Users should know about best practices, such as strong passwords, two-factor authentication, and recognizing phishing attempts.
- Ongoing training programs can empower individuals to become the first line of defense.
Robust Infrastructure:
- Implementing strong security measures, including firewalls, intrusion detection systems, and encryption protocols, helps fortify the underlying digital infrastructure.
- Regular patching and updates are critical to addressing known vulnerabilities promptly.
Incident Response Plan:
- Organizations should have a well-defined incident response plan to ensure a coordinated and swift response to cyber incidents.
- There should be a process to detect, contain, and recover from attacks, as well as effective communication and collaboration among stakeholders.
Collaboration and Information Sharing:
- Cyber threats are not limited by borders or sectors.
- Public-private partnerships and information-sharing initiatives help disseminate threat intelligence, foster collaboration, and strengthen the collective defense against cyber attacks.
Conclusion
By adopting a proactive and comprehensive approach to cybersecurity, we can safeguard our personal information, protect our businesses, and secure our critical infrastructure.
Together, we can build a resilient digital frontier that enables innovation, economic growth, and a safe digital environment for all.
Pingback: Defense in Depth: Cybersecurity Through Layered Protection - Skillie
Pingback: Use Case: Implementing Zero Trust Architecture - Skillie