Scenario:
As we all know how important defense in depth is for security, let’s try and understand how this works!
ABC Corporation is a large organization with a complex network infrastructure. They handle sensitive customer data, financial information, and proprietary business data. To ensure the security of their network and protect against potential cyber threats, they decide to implement a defense-in-depth strategy.
Defense In-Depth Strategy
ABC Corporation takes a layered approach to security by implementing multiple security measures across its network infrastructure.
Here’s how they apply defense in depth:
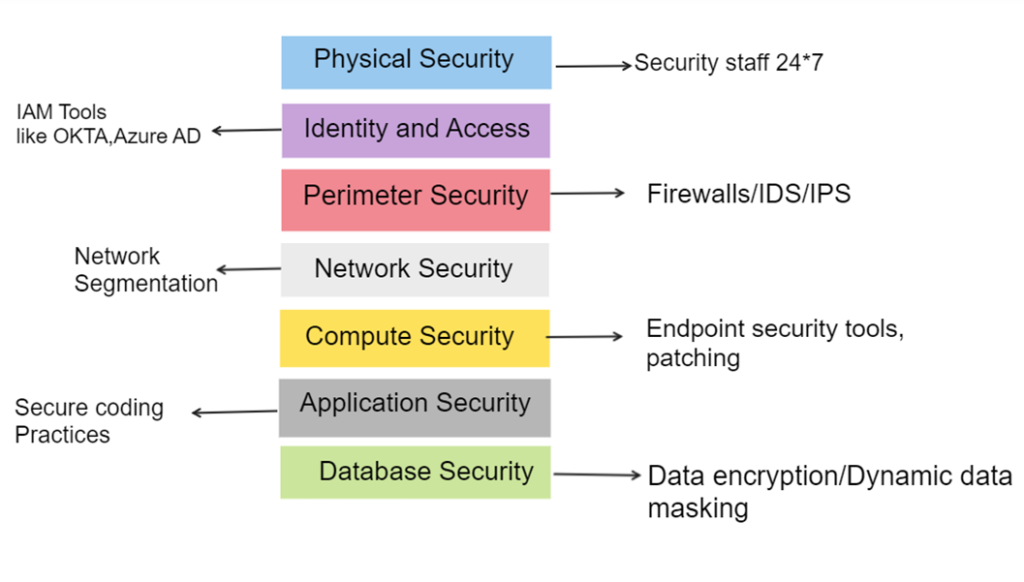
Physical Security
Security personnel are hired, and biometric verification is needed for identification. They work 24*7 in shifts.
Perimeter Security
A firewall or Unified Threat Management (UTM) system is deployed to filter and control incoming and outgoing traffic.
An Intrusion Detection System (IDS) and Intrusion Prevention System (IPS) monitor network activities for any suspicious behavior or potential attacks.
Identity And Access Management
ABC can opt for solutions like Okta, Azure AD, and OneLogin.
Access controls authenticate and authorized users appropriately,
Enforce the principle of least privilege, and manage privileged access to critical resources.
Network Security
VLANs, subnets, and DMZs are network segmentation techniques.
This divides the network into isolated segments, limiting the impact of a breach and preventing lateral movement.
This is at the network level
Endpoint Security
Endpoint security measures protect individual devices, such as desktops, laptops, and mobile devices.
Installation of security software, antivirus solutions, patching and host-based firewalls help with the same.
Application Security
It focuses on protecting web applications through techniques like web application firewalls (WAFs).
Follow secure coding practices to prevent common vulnerabilities in LOB applications of ABC Corporation.
Encryption
ABC Corporation applies data encryption and security mechanisms to its databases, ensuring confidentiality and integrity.
Education
Security awareness training is provided to educate employees.
These trainings talk about best practices, potential threats, and their role in maintaining a secure environment.
Pingback: Defense in Depth: Cybersecurity Through Layered Protection - Skillie
Pingback: Zero Trust Architecture: Redefining Security - Skillie