What is Zero Trust Architecture?
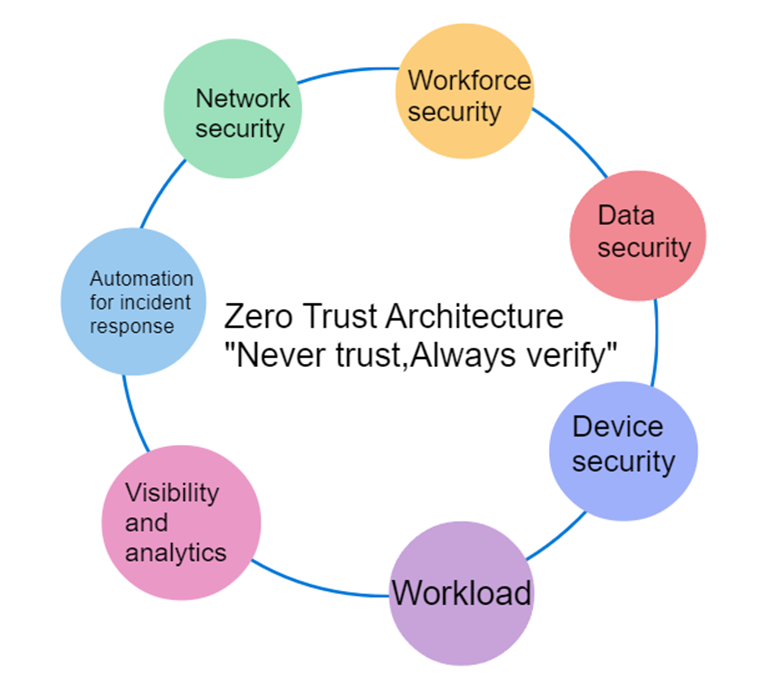
- Zero Trust Architecture or ZTA, is the modern-day approach to designing a security strategy. In today’s digital landscape, traditional security approaches that rely on perimeter defenses are no longer sufficient.
- Organizations face increasingly sophisticated cyber threats and a growing number of endpoints accessing their networks.
- In response, the concept of Zero Trust Architecture (ZTA) has emerged as a more effective security framework.
- Here we will understand Zero Trust Architecture and its fundamental principles and how they are revolutionizing the way organizations protect their critical assets.
- The concept of Zero Trust architecture was first introduced by John Kindervag, a former principal analyst at Forrester Research, in 2010.
- ZTA adopts a “never trust, always verify” approach, requiring continuous authentication and authorization for every user and device attempting to access resources, regardless of their location or network environment.
- This effectively counters the emerging “internal threat” issues that organizations face every now and then.
What are the key principles of Zero Trust Architecture?
The following are the key principles of ZTA:

Least Privilege
- Zero Trust Architecture operates on the principle of granting the minimum level of access required for a user or device to perform their intended tasks.
For e.g. a network administrator should only have admin rights, no architecture-level permissions.
This can lead to security breaches and because the administrator lacks architectural understanding, it’s dangerous to assign such permission levels because they lack the wisdom to use such high privileges.
- Access rights are defined based on identity, context, and the specific resource being accessed.
- This minimizes the potential attack surface and reduces the impact of a security breach.
Micro-segmentation
- ZTA divides networks into smaller, isolated segments, often referred to as microsegments.
- Each microsegment contains specific resources and is protected by its own set of access control mechanisms.
- By implementing micro-segmentation, organizations can contain potential threats and prevent lateral movement within their network, even if one segment is compromised.
- So even if a cyberattack occurs, it would not be able to progress further and we can contain it asap.
Continuous Assessment
- In Zero Trust Architecture, authentication is an ongoing process rather than a one-time event during login.
- User and device identities are verified repeatedly throughout the session, using factors such as multi-factor authentication (MFA), device health checks, and behavior analytics.
- This approach ensures that access privileges are dynamically adjusted based on the current context and risk level.
Continuous Monitoring
- ZTA emphasizes continuous monitoring and visibility into network traffic, user behavior, and device activities.
- This helps you to track unusual activities and act on them asap.
- Organizations leverage advanced analytics, machine learning, and threat intelligence to detect anomalies, identify potential security breaches, and respond quickly to emerging threats.
- Comprehensive visibility enhances situational awareness and enables proactive security measures.
Implementing Zero Trust Architecture
Implementing a Zero Trust architecture requires a comprehensive and well-planned approach.
Here are the key steps to consider when implementing Zero Trust principles within an organization:
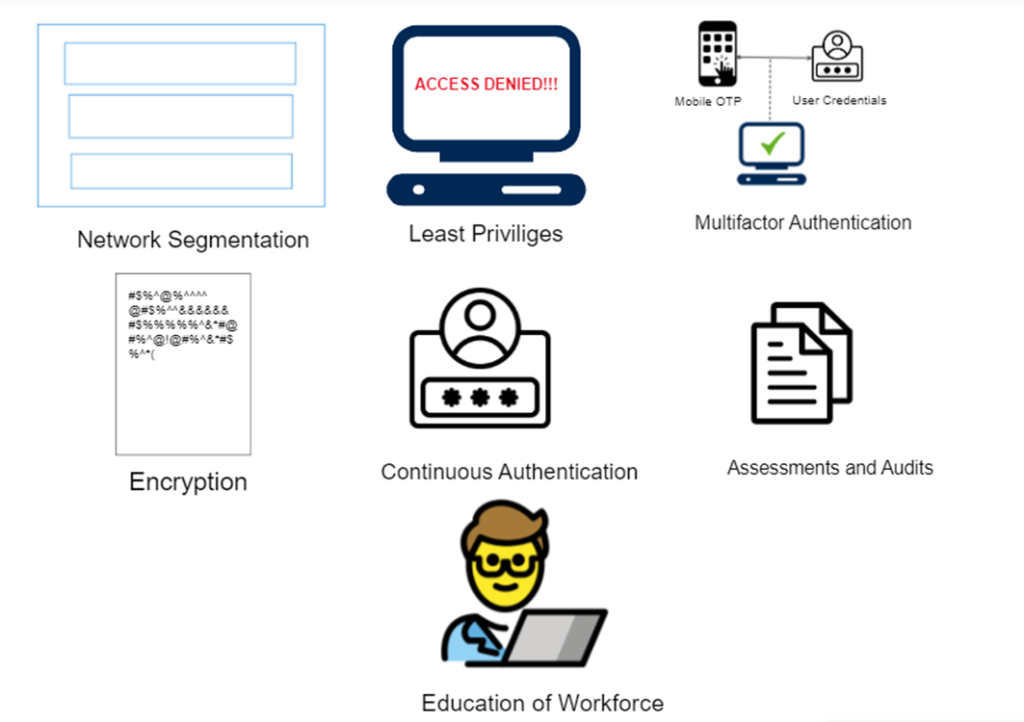
Define a Zero Trust Strategy
- Develop a clear strategy that outlines the goals and objectives of implementing Zero Trust.
- Identify the critical assets and data that need protection, assess current security measures, and define the desired security posture.
Identify and map data flows
- You should know how data moves within the organization and identify potential vulnerabilities and areas of risk.
- Analyse data at rest, in transit, and in use.
- Map out the data flows, including user access, network traffic, and application interactions.
- Appropriate security mechanisms should be there to protect the data whether it is at rest or in transit.
Establish strong IAM(Identity and Access Management)
- Users and devices should be properly authenticated and authorized before accessing resources.
- A strong IAM tool should be used for this.
- This also includes practices such as multi-factor authentication (MFA), strong password policies, and privileged access management (PAM).
Implementing Least Privilege
- Adopt the principle of least privilege, which grants users and devices only the minimum access necessary to perform their tasks.
- Limit privileges based on job roles, responsibilities, and the principle of need-to-know.
- Regularly review and update access privileges as roles change.
Network Segmentation
- Segment the network into smaller, isolated segments or micro-perimeters.
- This limits lateral movement within the network and contains potential breaches.
- Apply access controls and firewalls to enforce strict traffic filtering between segments.
Continuous Monitoring Analysis
- Deploy security tools and technologies to monitor network traffic, user behavior, and system activities.
- Implement user and entity behavior analytics (UEBA) to detect anomalous or suspicious behavior patterns that may indicate a security breach.
- Regularly review and analyze security logs and alerts to identify potential threats.
Data Protection
- Encrypt sensitive data both at rest and in transit.
- Implement strong encryption protocols and mechanisms to protect data from unauthorized access or interception. Use data loss prevention (DLP) solutions to monitor and control data movements.
Application Centric Security
- Implement micro-segmentation by segmenting applications and workloads into separate compartments with strict access controls.
- Apply security policies at the application level to ensure that only authorized traffic and interactions occur.
Continuous Authentication
- Implement continuous authentication mechanisms to monitor user behavior throughout their session.
- This includes technologies such as session timeouts, reauthentication prompts, and behavioral biometrics to ensure that the user’s identity and access level remain valid.
Regular Assessments and Audits
- Perform regular security assessments, vulnerability scans, and penetration tests to identify weaknesses and vulnerabilities in the Zero Trust architecture.
- Conduct periodic audits to ensure compliance with security policies and regulatory requirements.
Employee Education and Continuous Improvement
- Train employees on the principles of Zero Trust, the importance of strong security practices, and the role they play in maintaining a secure environment.
- Promote a security-conscious culture and encourage reporting of suspicious activities or potential security incidents.
- Monitor the evolving threat landscape and stay updated with emerging security technologies and best practices.
- Continuously refine and adapt the Zero Trust architecture based on new insights and lessons learned from security incidents.
- Implementing a Zero Trust architecture is an ongoing process that requires collaboration among different teams, including IT, security, and management. It is crucial to involve stakeholders from various departments to ensure a holistic and effective implementation of Zero Trust principles.
Conclusion
Zero Trust Architecture represents a paradigm shift in security, acknowledging the need to constantly verify and validate every user and device accessing critical resources.
By adopting a Zero Trust approach, organizations can significantly enhance their security posture in the face of evolving cyber threats.
Also, read Zero Trust Architecture vs Defense in Depth
Pingback: Zero Trust Architecture vs Defense in Depth - Skillie
Pingback: Devastating Consequences of Ignoring Zero Trust - Skillie
Pingback: Use Case: Implementing Zero Trust Architecture - Skillie
Pingback: Multifactor Authentication - Skillie