Defense in Depth, a concept rooted in military tactics, has emerged as a robust cybersecurity approach. In the ever-evolving landscape of cybersecurity threats, organizations must implement comprehensive security strategies that go beyond single-point solutions.
This strategy involves deploying multiple layers of security measures to protect critical assets and mitigate the risk of successful cyberattacks.
Here, let’s understand Defense in Depth and explore its key principles and benefits in fortifying organizational cybersecurity.
What are key principles in Defense in depth?
Layered Security Controls:
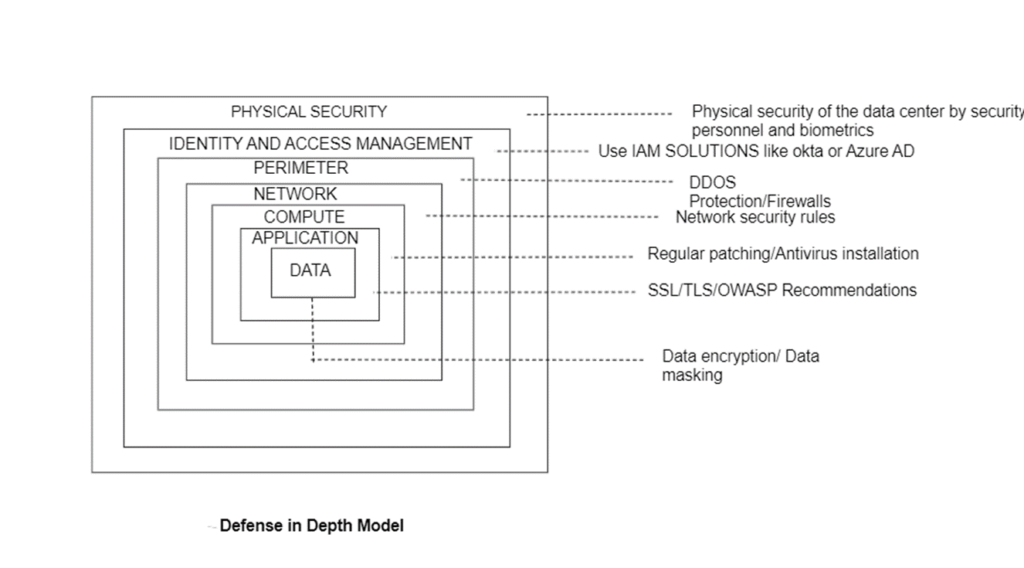
Defense in Depth is implementing multiple layers of security controls at different levels of an organization’s technology infrastructure.
These controls encompass various domains, including network security, access controls, endpoint protection, data encryption, and user awareness training.
Each layer provides an additional line of defense, making it more challenging for attackers to breach the system.
If something goes wrong at one layer, the other layer remains unaffected.
Redundancy:
- It promotes redundancy- if one layer of security is compromised, there are additional measures in place to mitigate the risk.
- Redundancy can involve having backup systems, redundant network connections, or even duplicate security controls.
- This maintains system availability during security incidents.
Diverse Defense Mechanism:
- A range of security technologies further strengthens the security posture.
- This includes firewalls, intrusion detection and prevention systems, antivirus software, secure coding practices, security awareness training, and incident response plans.
- By diversifying security measures, organizations can address vulnerabilities from multiple angles and better protect against evolving threats.
Continuous Monitoring and Response:
- Defense in Depth emphasizes the importance of continuous monitoring and real-time threat detection.
- Security teams need visibility into network traffic, system logs, and user activities to identify anomalies and potential breaches promptly.
- Organizations should have incident response plans in place to effectively respond to security incidents and minimize damage.
Why should we implement defense in depth?
There are genuine reasons for implementing defense in depth and why you should not ignore it!
Enhanced Security Resilience:
- By implementing multiple layers of defense, organizations strengthen their resilience against cyber threats.
- If one layer fails, there are additional measures to prevent or mitigate the impact of an attack.
Mitigation of Attack Surface:
- Defense in Depth reduces the attack surface by compartmentalizing the network and applying specific security controls at each layer.
- This approach limits the lateral movement of attackers, making it more challenging for them to gain access to critical assets.
- This helps security engineers to stop the attack and reduce the damages.
Adaptability to Evolving Threats:
- Cyber threats are constantly evolving, and attackers employ sophisticated techniques to breach security defenses.
- Organizations can adapt and respond to emerging threats by incorporating new security controls and practices as they become available.
Compliance and Regulatory Requirements:
- Many industry regulations and compliance frameworks mandate the implementation of multiple layers of security controls.
- Defense in Depth aligns with these requirements, aiding organizations in achieving and maintaining compliance.
Use case to understand the mechanism can be found here
Conclusion
Defense in Depth provides a robust approach to cybersecurity by implementing multiple layers of security controls, embracing redundancy, diversifying defense mechanisms, and continuously monitoring for threats.
Organizations can strengthen their security posture, enhance resilience, and mitigate the risk of successful cyber attacks.
Pingback: Use Case: Defense in Depth Implementation for Enterprise - Skillie
Pingback: Zero Trust Architecture vs Defense in Depth - Skillie
Pingback: Devastating Consequences of Ignoring Zero Trust - Skillie