Introduction
Multifactor Authentication is a process through which we confirm the identity of a user who tries to sign in. This is not just a regular authentication. It is a strong authentication mechanism.
Authentication has to be strong. There is something we call Authentication Factors that help to implement a strong authentication process. When we combine multiple authentication factors, We call it Multifactor Authentication.
It plays a key role in Zero Trust
So now, it’s not just about correct credentials. There is more to it.
Why Multifactor Authentication?
Authentication through credentials is common. However, it is not reliable anymore because one can easily share credentials. We should have a strong authentication mechanism that is hard to crack, so, we opt for Multifactor Authentication.
let’s understand what are Authentication factors.
Authentication Factors
Firstly, Authentication factors are used to verify the identity of individuals accessing a system, application, or service. Secondly, they provide an additional layer of security beyond just a username and password.
So, Here are some common authentication factors:
Knowledge-based factors
These factors require the user to provide something they know, such as a password, PIN, or answers to security questions.

Possession-based factors
These factors involve something the user possesses, such as a physical token, smart card, or mobile device used for receiving authentication codes.

Inherence-based factors
Also known as biometric factors, these involve unique biological characteristics of the user, such as fingerprints, iris or retinal patterns, facial recognition, voice recognition, or even typing patterns.
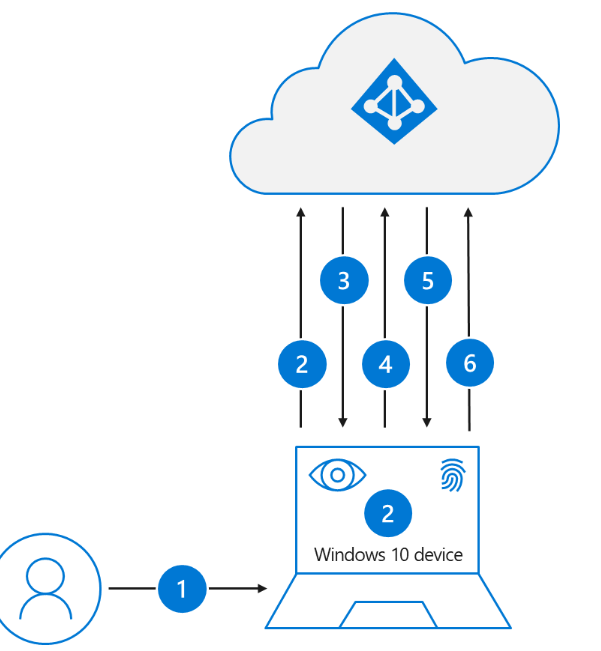
Source:https://learn.microsoft.com/en-us/azure/active-directory/authentication/concept-authentication-passwordless
Location-based factors
These factors determine the user’s location or the proximity of their device to a specific location using technologies like GPS, IP geolocation, or proximity tokens.

Time-based factors
This factor considers the time of authentication, usually in combination with another factor. Time-based factors include time-based one-time passwords (TOTP), where the user must provide a code generated by an authentication app within a certain timeframe.
Multi-factor Authentication
Multi-factor authentication combines two or more authentication factors to provide an extra layer of security.
For example, a combination of a password (knowledge-based) and a one-time code sent to a mobile device (possession-based) is a common MFA method.
The use of multiple authentication factors significantly increases the security of a system by making it more difficult for unauthorized individuals to gain access.
The specific factors implemented depend on the level of security required, the sensitivity of the information or resources being accessed, and the usability and convenience desired.
Pingback: Use case: Multifactor Authentication - Skillie
Pingback: Safeguarding Information with the CIA Triad - Skillie