It’s better to know about CIA Triad first. Click here to understand the concept
Case Study-Implementing CIA Triad
XYZ E-commerce Corporation is an online retail company that deals with a vast amount of customer data, including personal information, payment details, and purchase history.
As an organization committed to ensuring customer trust and maintaining a competitive edge, XYZ understands the criticality of implementing robust security measures to protect the confidentiality, integrity, and availability of customer data.

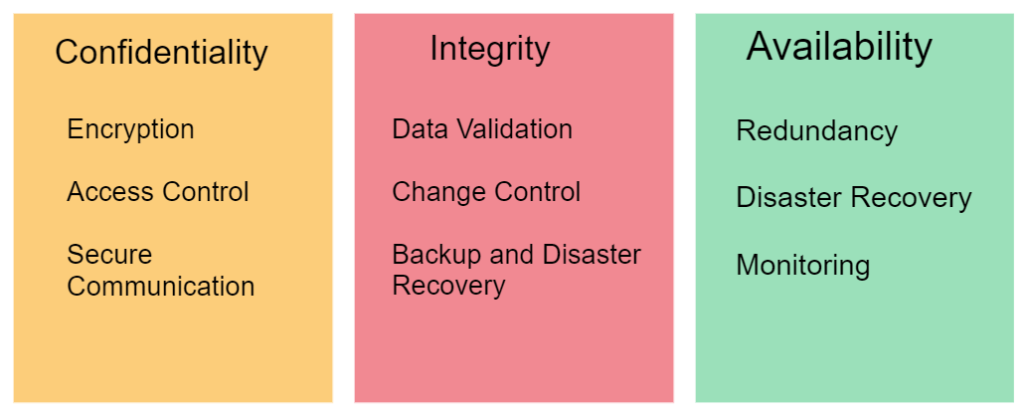
Confidentiality
XYZ E-commerce employs several measures to ensure that customer data remains private and only accessible to authorized personnel
Encryption
Data, both in rest and in transit is encrypted. This includes all sensitive customer data like personal information and payment details
The encryption algorithm is AES.
This ensures that even if the data is intercepted or accessed by unauthorized individuals, it remains useless to them.
Access Control
XYZ E-commerce implements strict access controls to limit access to customer data only to authorized employees who require it for their job responsibilities like database administrators. Role-based access controls (RBAC) are employed, granting different levels of access based on job roles and responsibilities.
This reduces the risk of unauthorized access or data breaches caused by internal employees or we can say that it reduces the risk of insider threats.
Secure Communication
Any communication channels used to transmit customer data, such as APIs or payment gateways, are secured using industry-standard protocols like HTTPS, ensuring that data is transmitted securely and cannot be intercepted or tampered with during transit.
Integrity
To ensure the integrity of customer data, XYZ E-commerce adopts various measures to prevent unauthorized modifications, data corruption, or accidental loss.
Data Validation
Before storing customer data, the e-commerce platform performs rigorous data validation checks to ensure the accuracy and consistency of the information. This includes verifying data formats, checking for anomalies, and validating against predefined business rules.
Change Control
Any modifications or updates made to the customer data are logged and audited to maintain a clear record of changes.
This helps detect and investigate any unauthorized or suspicious modifications to customer data, ensuring its integrity is preserved.
Backup and Disaster Recovery
Regular backups of customer data are performed, stored securely, and tested for successful restoration.
Backups are scheduled at various time intervals of the day.
However, the timing is decided by the backup team.
In the event of data loss or corruption, the backup system ensures that the most recent valid data can be recovered, minimizing any impact on customers.
Availability
Ensuring the high availability of customer data and uninterrupted access to e-commerce services is crucial for XYZ E-commerce.
They employ the following measures to maintain high availability.
Redundancy
The e-commerce platform is built with redundant systems and network infrastructure to eliminate single points of failure.
Data copies are placed over diverse infrastructure components that are resilient to single rack and data center failures.
This includes redundant servers, load balancers, and network connections.
In case one component fails, another takes over.
This minimizes downtime and ensures continuous access to customer data.
Disaster Recovery Planning
XYZ E-commerce has a robust disaster recovery plan in place that includes off-site backups, alternate data centers, and failover mechanisms.
This ensures that in the event of a catastrophic event or system failure, the e-commerce platform can quickly recover and restore service
Proactive Monitoring
The enterprise employs real-time monitoring and alerting systems to identify any potential issues or anomalies that may impact availability.
Further, This allows prompt detection and resolution of issues before they escalate and affect customer experience.
Conclusion
By prioritizing the CIA triad, XYZ E-commerce Corporation establishes a strong information security foundation for protecting customer data.
The implementation of CIA Triad demonstrates the enterprise’s commitment to maintaining customer trust, complying with data protection regulations, and safeguarding sensitive information from cyber threats.