Introduction
The CIA triad, a fundamental concept in information security, provides a framework for protecting valuable assets. In an increasingly digital world, where data is the lifeblood of organizations and individuals, ensuring the security of information is of paramount importance.
Data nowadays is the fuel that drives many businesses. So, it should always be protected.
It consists of three core principles – Confidentiality, Integrity, and Availability.
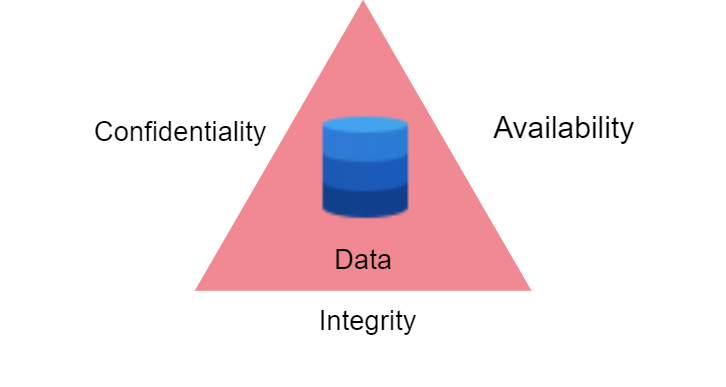
Here, we will explore each element of the CIA triad and its significance in safeguarding sensitive information.
Confidentiality
It refers to the assurance that in every circumstance, information is kept private and only accessible to authorized individuals or entities.
Confidentiality is crucial in preventing unauthorized disclosure or leakage of sensitive data.
How to implement Confidentiality?
Organizations often employ encryption techniques, access controls, and secure communication channels to maintain confidentiality.
By implementing measures such as MFA, data encryption, and user authentication, confidentiality is upheld, and data breaches can be mitigated.
Integrity
Integrity is to ensure that information remains accurate.
The idea is to protect the data from unnecessary modifications so that it is trustworthy for business use.
Data integrity guarantees that data remains intact, uncorrupted, and free from unauthorized modifications.
How to guarantee Data Integrity?
Organizations employ various mechanisms such as digital signatures, checksums, and data validation protocols to maintain data integrity.
By implementing access controls, version controls, and backup systems, organizations can prevent unauthorized tampering, accidental data loss, or data corruption, thus preserving the integrity of their valuable information.
Availability
Firstly, Availability ensures that information and resources are highly available. i.e., data is accessible and usable whenever needed by users.
Secondly, the access should be only for authorized users.
As Data availability is needed for all operations to continue that rely on data like online transactions. Data analysis etc.
How to keep Data Highly Available?
Organizations must ensure that their systems and networks are resilient to disruptions, downtime, or denial-of-service attacks to maintain availability.
Employing redundant systems, disaster recovery plans, and proactive monitoring can help organizations minimize the impact of potential service interruptions.
Availability also encompasses timely system updates, patches, and regular maintenance to avoid vulnerabilities that may compromise accessibility
Challenges and Concerns with CIA Triad
Implementing the CIA triad is not without challenges.
As technology advances and cyber threats evolve, organizations must adapt their security measures accordingly.
The increasing use of cloud computing, mobile devices, and Internet of Things (IoT) devices introduces new complexities and vulnerabilities.
In Addition, Balancing user convenience and security can also be a challenge, as stringent security measures might impede user productivity.
Finally, emerging threats such as social engineering and insider threats require organizations to adopt a holistic approach that includes employee education, risk assessments, and continuous monitoring.
Conclusion
The CIA triad provides a comprehensive framework for organizations to implement robust information security measures. By prioritizing confidentiality, integrity, and availability, organizations can protect themselves from unauthorized access, data breaches, and service disruptions. However, it is essential to recognize the evolving threat landscape and adapt security strategies accordingly. By continuously evaluating and enhancing their security posture, organizations can effectively navigate the challenges of the digital age and ensure the protection of sensitive information
Hi,
I intend to contribute a guest post to your website that will help you get good traffic as well as interest your readers.
Shall I send you the topics then?
Best,
Alvina Miller