Zero trust is the recommended approach to secure our corporate environment from all kinds of cyber-risks. This is a sample scenario inspired by the writer’s corporate experience.
Click here to understand Zero Trust.
Organization: JINDAL Corporation (Pen name for the article)
- JINDAL Corporation is a multinational organization with vast network infrastructure, multiple office locations, and a large remote workforce.
- To enhance its cybersecurity posture and address the evolving threat landscape, JINDAL Corporation decided to implement a Zero Trust architecture across its network.
- They have a hybrid cloud deployment(with Azure), deployed across the globe. They are using a few cloud services that we will get to know in this use case:
Scenario
- JINDAL Corporation recognized the need to strengthen its security measures due to the increasing frequency and sophistication of cyber attacks.
- By implementing Zero Trust principles, they aimed to mitigate the risks associated with traditional perimeter-based security models and better protect their sensitive data and critical systems.
Identity and Access Management (IAM)
JINDAL Corporation began by implementing a robust IAM system to ensure strong authentication and authorization mechanisms.
They are using Azure AD as the core IAM solution. Licensing is premium P2
They are using Azure AD for:
- Multi-factor authentication (MFA) for all employees, requires additional verification factors beyond passwords.
- Access policies were implemented based on the principle of least privilege, granting users only the necessary access permissions based on their roles and responsibilities.
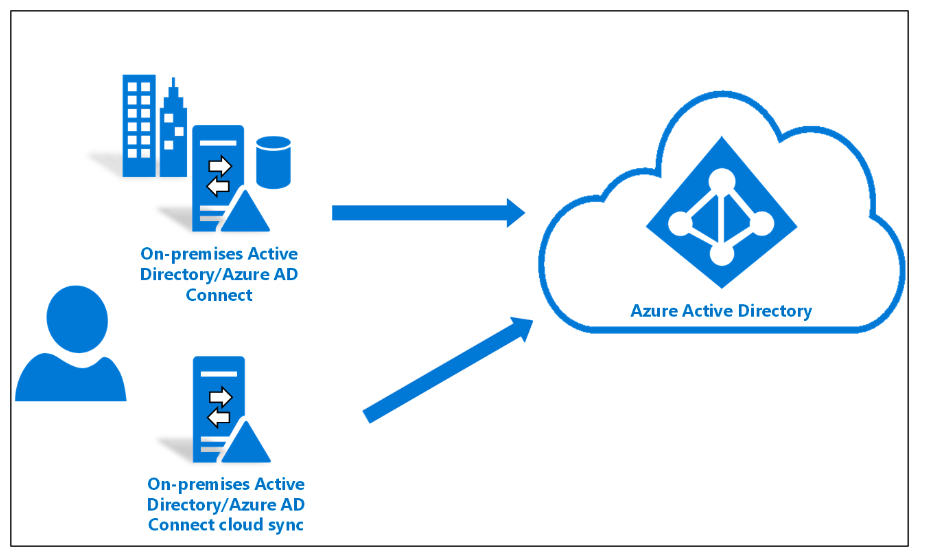
Source of image: https://learn.microsoft.com/en-us/azure/active-directory/hybrid/cloud-sync/tutorial-pilot-aadc-aadccp
Network Segmentation and Micro-Perimeters
- To limit lateral movement within their network, JINDAL Corporation implemented network segmentation and micro-perimeters.
- They divided their network into smaller, isolated segments or zones, each with its own access controls and firewalls to not blindly allow the traffic to move across the network.
- Lastly, this ensures if one segment was compromised, the attacker’s ability to move laterally and access other areas of the network would be significantly restricted.
Continuous Monitoring and Analytics
- JINDAL Corporation deployed a range of security tools like solar winds to continuously monitor network traffic, user behavior, and system activities.
- They utilized advanced threat detection solutions and user and entity behavior analytics (UEBA) to identify anomalous activities and potential security breaches.
- Real-time alerts and automated response mechanisms were put in place to enable swift action.
- As a result, in case of a security incident, an automated response acted up and controlled the attack, without causing any serious damages.
- They are using Microsoft Sentinel for SIEM and SOAR.

Source: https://learn.microsoft.com/en-us/azure/sentinel/overview
Application-Centric Security
- Recognizing the importance of protecting applications and workloads, JINDAL Corporation implemented application-centric security measures.
- Applications support HTTPS only.
- OWASP best practices are followed for application security.
- Users and devices are validated before granting access to the application
- This ensured that only authorized and authenticated users could interact with critical applications and sensitive data.
Secure Remote Access
- As a global organization with a remote workforce, JINDAL Corporation prioritized secure remote access.
- They implemented a Virtual Private Network (VPN) infrastructure and enforced Zero Trust principles for remote connections. This creates an encrypted channel to access applications and data.
- Employees accessing company resources remotely were subject to the same stringent authentication and authorization processes, ensuring that the organization’s security posture remained consistent regardless of the user’s location.

Source: https://simple.wikipedia.org/wiki/Virtual_private_network
Data Protection and Encryption
- To protect sensitive data, JINDAL Corporation implemented strong encryption protocols for data at rest and in transit.
- They deployed Symantec’s data loss prevention (DLP) solution to monitor and control data movements, preventing unauthorized access or leakage.
- Encryption mechanisms were applied to sensitive communications, ensuring confidentiality and integrity of data exchanged within and outside the organization.
The following table sums up everything:
| Security layer | Mechanism |
| IAM | Azure AD |
| Network | Micro segmentation and firewalls |
| Monitoring and Analytics | Solarwinds and Microsoft sentinel |
| Application Centric Security | OWASP best practices are followed for application security. User and devices are validated before granting access to the application |
| Secure Remote Access | VPN |
| Data Loss Prevention | Symantec DLP |
Regular Assessments and Audits
- JINDAL Corporation conducted regular security assessments, vulnerability scans, and penetration tests to identify and address any weaknesses or vulnerabilities in their Zero Trust architecture.
- External audits were performed to ensure compliance with industry regulations and internal security policies.
- Any identified gaps or vulnerabilities were promptly remediated to maintain a strong security posture.
Conclusion
Finally, JINDAL Corporation significantly enhanced its security posture and mitigated the risks associated with traditional perimeter-based security models.
The adoption of Zero Trust principles, including robust IAM, network segmentation, continuous monitoring, application-centric security, and secure remote access, ensured that the organization’s critical assets and sensitive data remained protected from evolving cyber threats.
Through regular assessments, audits, and continuous improvement, JINDAL Corporation maintained a strong security posture and demonstrated their commitment to safeguarding their assets and maintaining the trust of their customers and stakeholders